Hello Everyone, I hope everyone is doing great. In this write-up I am going to explain how did I found a No Rate Limit vulnerability in the Authentication Point that leads to Account Take Over in an OTT platform website. Its a private website so lets say the website is www.redacted.com
Before proceeding further, let me explain the impact to you, The lack of rate limit or no rate limit in the OTP (One-Time Password) sending mechanism poses a significant security risk to the company’s systems and its users. Without a rate limit, or if no rate limit presents in an application, an attacker could potentially launch a brute-force attack on user accounts, in which they try a large number of possible OTPs until they find the correct one. This could enable the attacker to gain unauthorized access to user accounts.
Here’s How I found it.
- Intercept the API request that sends OTP.
- Send the request to the intruder.
- Select the OTP as Payload.
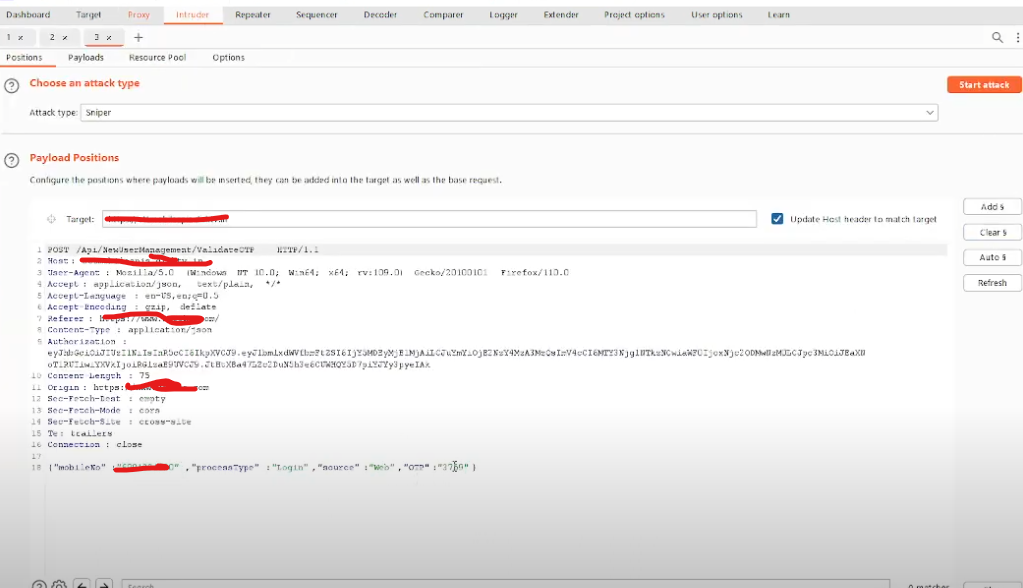
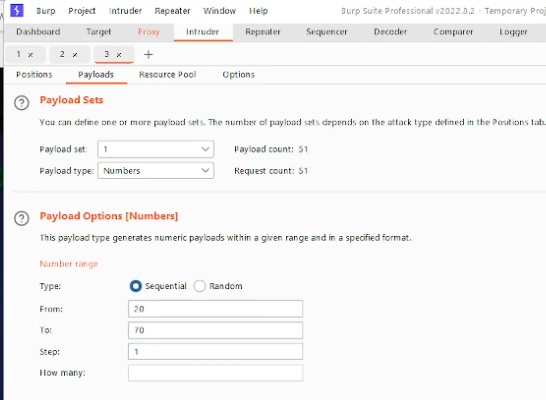
- Select Number as Payloads, and enter your desired amount.
- Select Attack.
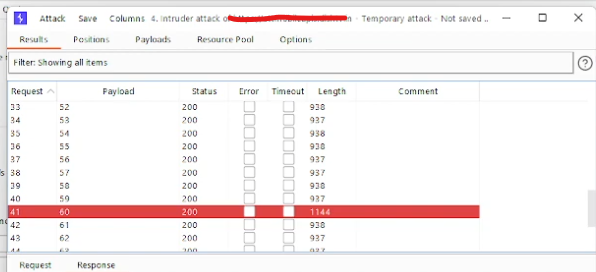
6. Check all the Responses are 200 OK and check for the length, the length with higher values as compared to others displays and hence you bypassed the OTP and got full access to the victim’s account.
I have reported the issue to the respected company, but they didn’t replied and fixed it silently. LOL
Thanks For Reading. Will post more of my write-ups.